The Power of Data Visualization Using Tableau
Cloud Security: Addressing the Risks and Challenges
Cloud security encompasses a comprehensive array of protective measures created to safeguard cloud-based infrastructure, applications, and data.
Its primary objective is maintaining comprehensive control over data and resources. This comprises:
- Preventing unauthorized access
- Safeguarding data privacy
- Fortifying defenses against external hackers and insider threats
- Ensuring the resilience of cloud workloads against malicious disruptions
Why Do You Need Cloud Technology Security?
As organizations increasingly rely on cloud solutions, ensuring robust security measures is essential to protect sensitive data and maintain compliance.
- Cloud Misconfigurations: Improperly set up systems can allow attackers unauthorized access to sensitive resources, often due to human error or inadequate automation templates.
- Data Privacy & Confidentiality in the Cloud: Improperly secured cloud storage or poorly planned migrations can expose sensitive data, risking regulatory fines and reputational damage.
- Social Engineering & Credential Theft in Cloud Environments: Attackers exploit widely used cloud apps to trick employees and steal credentials, jeopardizing data security.
- Meeting Stringent Compliance Needs: Cloud environments pose challenges in meeting compliance standards due to limited visibility and distinct infrastructure compared to traditional data centers.
Top Cloud Data Security Challenges
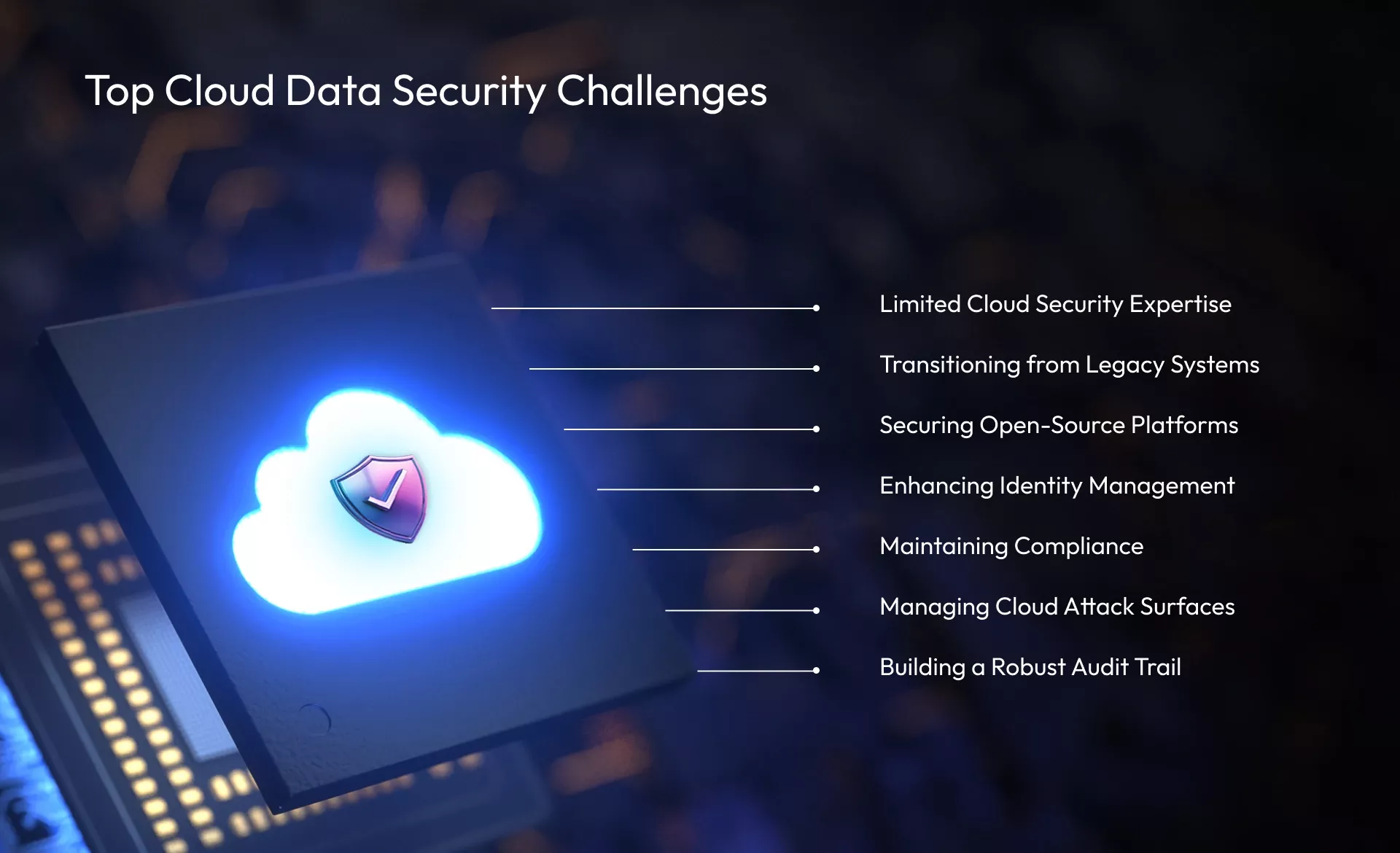
Challenges in Accessing Cloud Security Expertise
Specialized knowledge in cloud architecture and security is crucial. However, the demand for skilled professionals, especially in addressing security issues in cloud computing, surpasses the current availability.
As a result, organizations increasingly depend on external advisory and managed services for the deployment, maintenance, and security of their cloud resources.
Transitioning from Legacy to Modern Security Solutions
Embracing new technologies like cloud services necessitates a shift in security approaches.
Cloud infrastructure, characterized by a global and accessible network, challenges traditional security models centered around network firewalls and on-premises credentials.
To effectively address cloud security concerns, businesses must evolve and embrace concepts like Zero Trust Architecture.
This approach recognizes the ubiquity of cloud resources and the demand for remote access. Resultantly, it emphasizes security at the application level.
Incorporating Security in Open-Source Platforms
In cloud computing, DevOps and security teams favor open-source technology for its accessibility and customization benefits.
However, while it speeds up development, it also presents challenges.
Without certification from cloud providers and official support, open-source code can expose businesses to vulnerabilities and integration issues.
The lack of formal support increases the risk of misconfigurations, making a strong security strategy essential for organizations adopting open-source solutions.
Elevating Identity and Access Management
IAM (Identity and Access Management) poses a crucial challenge in securing the cloud.
With users accessing resources at the application or modular level, granular control becomes imperative.
In environments without single sign-on (SSO), each user is verified for individual applications. This necessitates investments in technology and personnel for -
- precise control
- secure storage of identity credentials
- comprehensive activity tracking
This aids in enhanced logging and system visibility.
Ensuring Ongoing Compliance Amidst Cloud Evolution
Regulatory and industry data management standards, such as HIPAA and PCI DSS, were established in the pre-cloud era.
Despite the shift to cloud storage and processing, compliance obligations endure. Organizations under these mandates need to maintain internal security governance. They also need to validate that their technology providers, including cloud services, align with regulatory data security requirements.
Strategizing Attack Surface Management in the Cloud
Whether employing SaaS or IaaS platforms like AWS, cloud systems introduce unique challenges to Attack Surface Management (ASM).
Additional endpoints, applications, and third-party resources create potential attack vectors and visibility issues.
For example, a department using an unreported CRM SaaS solution adds an unmonitored entry point. Proactive cataloging and monitoring strategies are essential to address these challenges.
Establishing an Effective Audit Trail
A real-time activity log is essential for incident response, helping security teams quickly identify and isolate cloud security breach sources.
This is crucial for organizations with compliance requirements.
Centralizing this information in the cloud is challenging due to dispersed resources. Additionally, cloud applications are often provisioned outside of IT management, leading to reduced visibility and auditing capabilities.
Top Cloud Data Security Risks and Threats
To better safeguard your organization's data, it's important to understand the top cloud data security risks.

Zero-day attacks
The widespread use of open-source software and platforms like AWS, Azure, and Google Cloud increases the risk of vulnerabilities being exploited. Hackers target these weaknesses, prompting administrators to quickly implement updates and maintenance to prevent attacks.
Missteps in Cloud System Configurations
Cloud technology security vulnerabilities often arise from misconfigurations. These include granting excessive access privileges or using default, easily guessed credentials. The complexity of cloud infrastructure and integrations makes these errors common.
Securing Against Online Account Hacking
Cloud applications often rely on basic username-password authentication, making them vulnerable to phishing, weak passwords, and brute-force attacks. Strengthening credential management is essential to prevent unauthorized access.
Mitigating Insider Threats
Without robust Identity and Access Management (IAM) or Zero Trust measures, trusted users can become threats, risking data theft or malware attacks. Insider negligence, like sharing unencrypted files or exposing credentials, also poses significant risks that must be mitigated.
Navigating the Challenge of Malware in the Cloud
Cloud applications simplify resource sharing but increase malware risks, as file exchanges create opportunities for malicious code to infiltrate and spread across the network.
Addressing Data Loss in Cloud Services
Data loss in cloud environments can result from ransomware, where hackers encrypt or delete data, or migration errors during transitions. The ease of sharing files and apps also heightens the risk of sensitive data exposure through negligence or malicious actions.
Navigating Non-Compliance Risks in Cloud Data Security
Managing compliance in the cloud is challenging. Non-compliance can lead to legal consequences, fines, and reputational damage. Failing to vet providers or implement proper security configurations risks customer privacy and regulatory penalties.
How to Effectively Manage Cloud Technology Security Risks and Challenges
Given that many security risks in cloud computing manifest at the application level, organizations need a comprehensive strategy to safeguard applications and resources.
Implementing multi-factor authentication (MFA) is one such measure, adding an extra layer of protection against user-account-based hacks through biometrics or hardware verification.
Continuous visibility and access management play pivotal roles in cloud security. Integrating Cloud Infrastructure Entitlement Management (CIEM) technology enables automated threat detection, activity monitoring, and access management across multi-cloud and hybrid environments.
It facilitates precise permission settings, enforces the principle of least privilege, and streamlines compliance audits, powering digital transformation through the cloud.
To mitigate negligence incidents, companies should prioritize awareness training covering phishing scams, credential management, and handling sensitive cloud data.
Robust governance practices, including policies promoting strong passwords, regular cloud system backups, frequent access audits, and timely updates or patches for software applications, further contribute to a resilient cloud security posture.
Email us or Talk to us at +91-98367-81929 or Simply Contact Us through the website.
Let's Connect